
|
|
ICT-Hotlist Topic
How to: monitor Windows DNS servers for use of certain server names.
Published : 2014-06-02.
Last updated : 2020-11-15.
Of course one can use network sniffer software such as Wireshark or
other tools1 to monitor the DNS traffic for certain server name requests. The standard default debug logging of the DNS service can give
a quick indication without installing additional software.
Steps
- On the DNS server turn on Debug Logging (select properties on the DNS-Service) and set the following properties:
-
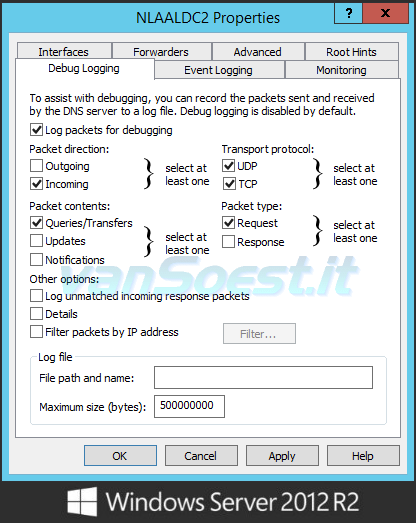
Windows 2012 r2 DNS server properties dialog showing the required Debug Logging options.
- The default logfile can be found here: %systemroot%\System32\dns\Dns.log
- The log contains entries in the format
- Date (month,day,year)
- Time
- Don't care
- Don't care
- Don't care
- UDP the protocol used
- Rcv it is a request to the DNS server
- Originating IP-address
- Don't care
- Q type is query
- [] Don't care
- Address type A => IPv4 AAAA => IPv6
- The requested domain with length denotifiers (PASCAL style)
-
5/31/2014 5:00:28 PM 1290 PACKET 0000000006F3D750 UDP Rcv 10.1.1.13 000a Q [0001 D NOERROR] A (8)vansoest(2)it(0)
5/31/2014 5:00:28 PM 1290 PACKET 00000000070EEED0 UDP Rcv 10.1.1.13 000b Q [0001 D NOERROR] AAAA (8)vansoest(2)it(0)
This example shows a DNS request from the system with ip-address 10.1.1.13 (can be IPv4 or IPv6 address format) requesting the ip-address for vansoest.it
Just filter the log on the server name you need (for example "vansoest") and you have a list of systems still referencing the server.
No reboot or restart of the DNS server and service required.
Kevin Manning of Comparitech was so kind to report a broken link about Microsoft's Message Analyzer that is discontinued. On this site you can find an overview of packet sniffers
Scripts and programming examples disclaimer
Unless stated otherwise, the script sources and programming examples provided are copyrighted freeware.
You may modify them, as long as a reference to the original code and hyperlink to the source page is included in the modified code and documentation.
However, it is not allowed to publish (copies of) scripts and programming examples on your own site, blog, vlog, or distribute them on paper or any other medium, without prior written consent.
Many of the techniques used in these scripts, including but not limited to modifying the registry or system files and settings, impose a risk of rendering the Operating System inoperable and loss of data.
Make sure you have verified full backups and the associated restore software available before running any script or programming example.
Use these scripts and programming examples entirely at your own risk. All liability claims against the author in relation to material or non-material losses caused by the use, misuse or non-use of the information provided, or the use of incorrect or incomplete information, are excluded. All content is subject to change and provided without obligation.
|










 Back to the ICT-Hotlist...
Back to the ICT-Hotlist...